Why would a hacker attack a nonprofit website? Hackers are on the lookout for vulnerable and valuable websites and nonprofits are some of the best of both worlds.
If your nonprofit-related website has been compromised, try not to take it personally. In my experience at HackRepair.com, I have worked on thousands of hacked websites. It’s almost never personal.
In this article, I’ll cover the basics of website account security and describe how you can greatly increase the security of your nonprofit’s website right now. We’ll cover the following topics:
- How do hackers get personal information?
- Why do hackers hack websites?
- How do hackers hack?
- What is segregated hosting and why is it important?
- What passwords should I change?
- Have I been hacked? How can I fix it?
- What is backdoor malware?
- How can I help prevent my website from being hacked?
How do hackers get personal information?
There are a variety of ways your website can get hacked and each comes with its own special terminology. In this article, we’ll talk about a few specific types of hacking to which your nonprofit is vulnerable.
One of the most important things to look out for is Phishing. Phishing is the fraudulent practice of masquerading as a reputable company in order to trick others into revealing confidential information. This kind of hacking comes in the form of a phone call, email, text message, or any other type of communication. The idea is to gather the confidential information necessary to hack into important systems.
Once hackers gain access to your systems, they dive in deeper. Online, people commonly run into SEO SPAM, also known as SPAMdexing or injecting backlinks. It’s an attempt to manipulate search engine rankings by black-hat SEO hackers. These kinds of hackers add links or content to a legitimate website to help increase the search engine position of another website.
Harvesting credit cards is another common goal of hackers because nonprofits often collect online donations on-site. Harvesting credit card numbers is done by injecting code into a payment page in order to “sniff” credit card information while it’s entered. This method of hacking is the reason that an SSL certificate is required to collect payment information online.
Larger nonprofits especially are also sometimes targeted by DDoS or “distributed denial of service” attacks. Usually, when this happens, someone gathers a large number of “bots” to rapidly “attack your domain and overload the server, resulting in the website going down. Your SEO declines the longer your site remains down.
You might also encounter Badware or drive-by downloads. These refer to the unintentional download of malicious code into a computer or mobile device. The scary part is that a click or other action may not be required to inject malicious code into the device. Finding these kinds of hacks is more difficult because you may not be aware that it happened.
Other kinds of hacking you might encounter include:
- Ransomware: a form of virtual blackmail, where malicious software is employed to lock data until a ransom fee is paid.
- Malware: malicious code injected to cause harm to a website, its reputation, or devices connected.
- Website Defacement: changing the content on a website with malicious intent.
Why do hackers hack websites?
Believe it or not, hacking websites brings in big money. According to security researchers, Some hackers make more than $80,000 a month. It’s no wonder hackers continue to bring down websites, but why nonprofits?
Nonprofit websites are generally targeted by hackers for a variety of reasons. Some of those reasons are:
- Nonprofits are more often maintained by part-time volunteers with limited WordPress expertise.
- Well-maintained religious-based websites have better-than-average domain authority, credibility, and readership, which is especially appealing to black-hat SEO hackers.
- Nonprofit websites’ donation forms are a potential credit card harvesting center.
Essentially, nonprofit websites are usually not as well maintained, have high traffic and domain authority, and pass along credit card information.
How do website hackers break into a website?
Most nonprofits have less security on their website than they think they do. You may think your website is secure because your web designer is reputable and experienced. That’s not always the case. Design and website security don’t always go hand in hand so designers don’t always set up the security of your website thoroughly or train you on how to continue to do so after they’ve finished their project.
In my own experience over the past decade, over 80% of all the compromised websites that were hacked as a result of hackers taking advantage of exploits through either:
- Outdated plugins.
- Outdated themes.
- Poor password management or “key control.”
The majority of exploited website accounts I’ve encountered were compromised in one of two ways:
- The hacker either injected malware into the website database.
- The hacker used SEO SPAM, injecting text or code into posts and web pages.
Once hackers have a foothold into a website’s account they rarely give it up easily. Hackers often hide their backdoor scripts in various places throughout the hosting account so they can get back in when you discover one of them. I’ll cover backdoor scripts a bit later, but this is why it’s essential to set up your hosting properly from the beginning.
What is segregated hosting and why is it important?
Many hosting providers offer unlimited hosting packages, allowing you to host multiple websites on the same account. This is a budget-friendly technique, but it’s not a best practice. There’s a common misunderstanding among website owners about the dangers of hosting multiple websites within a single shared account.
Many people have fallen prey to unlimited shared hosting account services. On the surface, it seems like an unlimited shared hosting account is an efficient and low-cost way to host multiple websites within a single website account. In reality, this type of service is akin to renting office space where all of the internal office doors share the same front door key. Once someone gets into one website, they can also gain access to all the others.
If you are hosting multiple WordPress websites within a shared hosting account, your risk of a hack is exponentially greater than a website hosting account with a single WordPress installation. For this reason, segregating each website into its own separate hosting account is an important long-term website security strategy.
What passwords should I change?
This brings us back to my earlier note about poor “key control,” or password management. If your hosting accounts aren’t segregated, one password is the key to multiple websites. Even for segregated hosting accounts, a single website account on its own hosting account may have dozens of sub-passwords for users to login, access to billing FTP, etc. Each of these is a potential entry point for hackers.
If you are working to improve your organization’s password management I recommend locating and periodically updating each of the passwords below at least every few months:
- Your web hosting company’s “billing” login password.
- Your web hosting company’s website control panel (cPanel, Plesk, et al.).
- All FTP passwords within your website’s hosting account control panel.
- All WordPress user account passwords.
- Your organization’s social media accounts as well (Twitter, Facebook, et al.).
- Email client login passwords for all users.
Nonprofit organizations, in particular, are susceptible to password “leakage.” In addition to phishing attacks, nonprofits also often see a lot of turnover. The roles of volunteers within a nonprofit organization may change regularly, making both real-world physical security and website password security a challenge. Changing your passwords often and also ensuring you have no inactive user accounts are key details to include in your website security strategy.
While reviewing a client’s list of WordPress user accounts, look at what I stumbled upon:
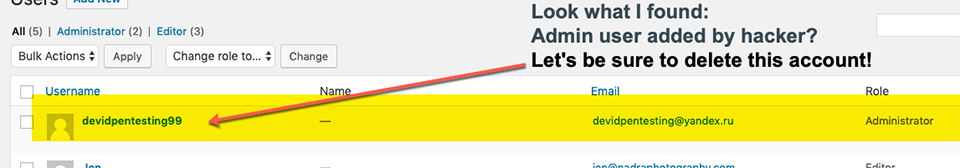
Generating fake administrator accounts is one way hackers can gain access to your website and insert malicious code and SEO SPAM. Keeping an eye on your accounts and ensuring all administrators change their passwords often is crucial, but it’s not the only way to prevent your website from attacks.
Have I been hacked? How can I fix it?
Normally, a website hacker’s strategy is injecting malware or malicious text into files or web pages. This injected code can do any number of things, like redirecting site visitors to other websites; advertising text or links; or harvesting visitor data. If you think that your website is acting strangely or redirecting someone elsewhere, then you may have been hacked.
Today’s websites are made from a mix of a few files to thousands of files. That’s a lot of hiding places to consider when reviewing a compromised website account. And nearly all of these files, from text files to PHP files and even images, may harbor malicious code. The trick is knowing what to look for.
Hacker files or code injections most often fall into one of three categories:
- Backdoor PHP scripts.
- Malware injected into legitimate files or databases.
- Or a combination of backdoor and malicious text or code injections.
When reviewing a recently hacked website I always start by sorting the directories and files within a website by date. With code injections, it’s often possible to quickly identify compromised files by viewing the text within the most recently changed files.
Theme files like the 404.php, functions.php, and header.php are commonly exploited files, example below:

But if you have any concerns at all, you should probably call an expert because there are creative and difficult to diagnose hacking techniques.
What is backdoor malware?
Backdoor malware is a script or code injected into legitimate files that give hackers access to add or edit the website remotely. Once in place within a website, these files or code injections may allow hackers unrestricted access to an account until they’re removed.
With the number of places a hacker may hide malicious code within a website, you can’t assume anything when it comes to locating and removing backdoor scripts. Every file and directory must be carefully reviewed for signs of malicious content. Some of the signs to look for include:
- New files added to your root directory that WordPress didn’t add on its own (generally you don’t need any additional files in your root aside from the default WordPress files).
- Your site suddenly performing much more slowly or getting 500 server errors continually.
- Your host might reach out to you about suspicious traffic to your website. If you don’t know why your site would have a spike in traffic, it’s likely related to an attack of some sort.
In the case of WordPress, even the latest malware monitoring security plugins may often miss or misidentify these files. Written by financially-motivated black-hat hackers, backdoor scripts often require a bit more effort to identify than running an off-the-shelf malware scanner. Human eyeballs haven’t yet been automated out of this job so it still requires a manual review. If you don’t know how to read code, then you may need the help of an expert.
Below is an example of hacker code injected into a legitimate WordPress file, which allows the hacker to pass commands along to another file added by the hacker:
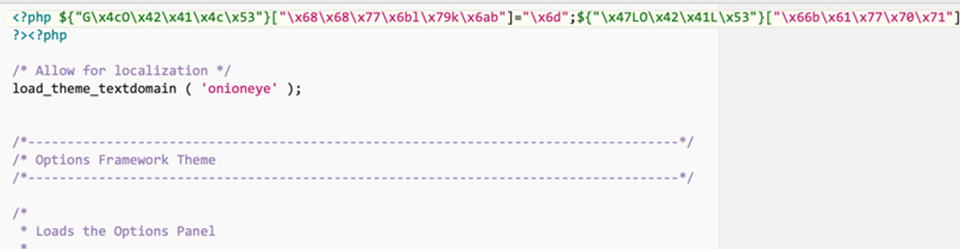
While it’s virtually impossible for a non-developer to recognize malicious code, things like the above stand out as obvious to developers. But if you notice code that you can’t read out loud very well — like the code on the first line above, for example — it would be best to reach out to a developer and ask them to review the file and remove the code.
How can I help prevent my website from being hacked?
With all of the ways hackers can embed themselves in your website, sometimes it’s impossible to remove the damage done. It’s best to prevent them from gaining access in the first place.
There are four actions you can take today to greatly improve the security of your website. Take the following four steps right now to decrease the likelihood your website will be compromised by hackers.
- Backups. Maintain a weekly automated backup of your website to a cloud service account like AWS, Google Drive or Dropbox. Make sure this is stored away from your website’s hosting server database. While you may not be able to monitor your website every minute of every day, a solid backup program will help turn a potential disaster into a one-click-to-recover insurance policy. For WordPress, try one of these plugins: UpdraftPlus, BackupBuddy or JetPack Backups.
- Updates. With content management systems like WordPress, the regular updating of your website’s plugins, themes, and WordPress core software are required steps in improving the security of your website and hosting account. These update frequently and don’t always go smoothly. So you have to log in on a regular basis and ensure your software is up to date and the front-end is still working as it should.
- Monitoring. Constantly monitor your website for security breaches. If your website was built with WordPress, there are a number of well-regarded security plugins to choose from. WordPress security plugins are not foolproof but they may help reduce the impact of bad bots and automated intrusion attempts by monitoring and notifying you as it happens.
- Management. And lastly, use a secure password management system to save passwords. This is a great way to reduce our very human tendency to use the same password for every website we password protect. It’s useful for randomizing and changing your passwords frequently.
Hacked? Don’t Panic. Call an Expert.
Nonprofits who rely on online fundraising may be more vulnerable to hacking, but when it happens don’t panic. If you haven’t yet set up these safety measures and your site was taken down, you can always call an expert. They’re the best option to get your site back up as fast as possible.


